Before addressing the matter proposed in our headline let’s put a few disclaimers out there for the sake of legality: Almost everywhere around the world the act of having access to the personal computer of a third party without their approbation is considered a felony and a prosecutable act by law enforcement agencies. However, doing so with legal permission is one of the many protocols used by many computer system companies to provide customer support. If you feel the need to learn about the legal aspects regarding the use of RAT systems, it would be better if you consult a lawyer or do some research online on your country.
With that little tidbit out of the way not we can go over the subject. RAT is an abbreviation for “Remote Administration Tool.” It is also known by another name that it doesn’t sound pretty at all: Remote Access Trojan. While the code has been around for quite some time, it’s always evolving and changing to adapt to new forms of blockage created by OS developers. They are regarded as one of the most dangerous types of malware around the world because it gives full access to your personal computer and everything it holds in it. The attacker can infect your PC with other forms of malware, or they can just steal your information.
How do I use a RAT on my End?
Personal purposes or motivations aside, this written tutorial is being posted with educational purposes in mind. If you want to use a RAT, you need to have some basic knowledge about hacking tools and the terminology used to handle these tools. A quick Google search will give you most of what you need in this regard. Our guide is offered for novice users, but you should have a handle on these requirements before attempting to use this program. The first you need to do is add additional ports to your router. The default login information is “admin” for an username and “password”. By creating a new TCP and a UCP port you will have to rename each one with different usernames and passwords for both. After doing that you will need to use a global port range of any number that is different from the one you are using. We recommend setting the base port at 1604 and save the settings.
What Should I do Next?
You need to make sure that ports you just created are open and functional. There is a tool called “CanYouSeeMe” (Do a Google search to access it) that can be used to check if the setup worked if the site gives you the green light of approval you are good to go. If it doesn’t this is what you can do to solve it: First, recheck the setup of the router and make sure it’s set just we told you. There might be an issue with remnants of software previously installed in your machine or simply outdated hardware that prevents you from getting the opening you need. Try changing the base port to different numbers until you get one that it’s working properly. If you need to work fast, you might be able to force your way in using a tool called “Port Format Wizard” that will give you 15-minute access to the port you are looking to connect with.
Are There Any Considerations Up to This Point?
Yes, setting up these ports should never be attempted on virtual environments since doing so can create significant damage to the mainframe of your OS. After having your ports set you will have to work fast unless you are paying for the premium options of the tools we offered previously. You need to set up a dynamic IP so you won’t have to update your connection continually. To make that happen, you can use a tool called “NoIP.” This will also keep you safe from being tracked by law enforcement agencies.
Noted, What’s Next then?
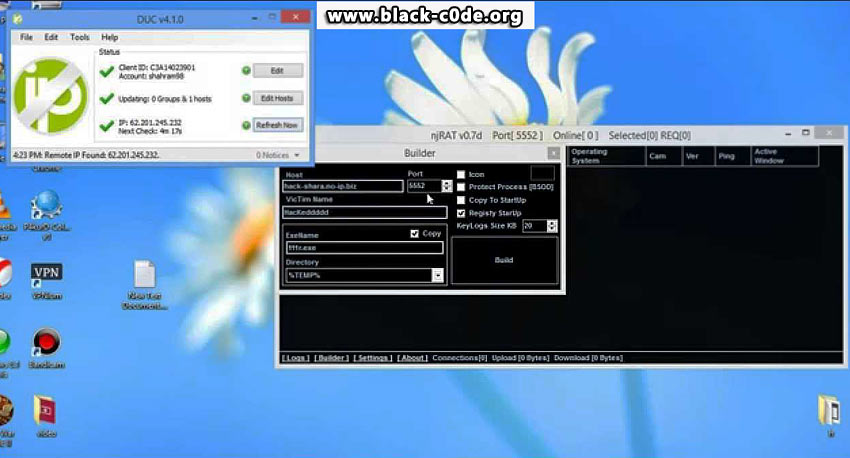
NoIP will allow you to create a client account with a hostname that can be set as your main website. You will be able to modify your IP address using the Dynamic Update Client option located in the tab of utilities. Your computer will synchronize instantly with the dynamic IP, and the address will be changed on specific time settings after you save the settings in the interface. Now it’s time to download the RAT finally. Given the nature of this program and the fact that is considered malware, finding one that actually works it’s tough for many newcomers.
The best piece of advice we can pitch in right now is never to use RATs that come encrypted, they are the worst type of scam, and they will probably link tour computer to a network of decentralized utilities, and you won’t even be aware of it. We recommend using the DarkComet or the njRAT utilities since they are some of the most trustworthy in the field. Beware though. If you work with the latest version of the known OS or if you have strong settings on your antivirus and firewalls, these programs will be detected as the malware they are and dealt with accordingly.
That Sounds like a Problem, what can I do About it?
The answer is straightforward but also one that many people don’t like: You need to deactivate all your defenses to launch the RAT program properly. You will also need to build firewall exceptions manually. Google is the one with the most robust defenses, so we recommend using Opera to manage the online setup. As for the arrangements that need to be done on your PC, there are quite a few tutorials on YouTube that can guide you about how to add expectations on your firewalls, make sure to look for one that goes with your current OS. After you are done with this part, it’s time to get your hands dirty by using any of the RATs recommended previously to create the backdoor that will give you access to the other system you are targeting. You will have to name your file, set the attributes, name the server, set the targeted IP to answer back to your dynamic IP, and create the icon that will set the trap.
Final Recommendations
You can add an extra layer of security on your end if you add an encryption tool to mask your dynamic IP. We recommend using one named “Aegis” to do the job. Leaving any traces can make people go over your steps and target you back if they know what they are doing. You can also use a VPN for the sake of it as a final layer to cover up your fake identity. Remember that using these tools is something shady at best, so don’t go crazy with it by trying to hack into the computers of any big corporations. They know how to fight back these online menaces, and they also have endless legal means to deal with you if you get in trouble with them.

